January 22nd, 2026 by William Wentowski
The Rising Tide of Cyber Threats
Cyber threats are no longer a matter of "if" but "when." As businesses increasingly rely on technology and data, the potential for cyber attacks and data breaches grows exponentially. At BTS Technologies,...
Read Full Story »
Tags: communication, cyber security, data breach
Posted in: Cyber Security
December 20th, 2025 by William Wentowski
From customer information and financial records to proprietary research and operational data, the information stored in your company's systems is invaluable. Yet, many businesses underestimate the importance of robust data backup and business...
Read Full Story »
Tags: data breach, data management, firewall
Posted in: Cyber Security
December 17th, 2025 by Roger Wentowski
Businesses of all sizes are increasingly reliant on digital technologies to operate, communicate, and innovate. While this digital transformation has brought unprecedented opportunities, it has also exposed organizations to a new frontier...
Read Full Story »
Tags: backup and disaster recovery, cyber security, data breach
Posted in: Cyber Security
October 6th, 2025 by William Wentowski
Understanding the Growing Need for Cyber Security Insurance
Businesses of all sizes face an ever-increasing threat from cyber attacks. As technology evolves, so do the tactics employed by cybercriminals, making it crucial for organizations...
Read Full Story »
Tags: communication, cyber security, data breach
Posted in: Cyber Security
September 16th, 2025 by William Wentowski
With cyber threats evolving at an alarming rate, organizations need robust strategies and reliable resources to protect their digital assets. One such valuable resource is the Center for Internet Security (CIS), a nonprofit entity dedicated to enhancing...
Read Full Story »
Tags: cyber security, monitoring, network
Posted in: Cyber Security
June 16th, 2025 by Roger Wentowski
In an era where cybersecurity threats continue to evolve at an alarming pace, small to mid-sized businesses (SMBs) often find themselves caught between increasingly sophisticated attacks and frustratingly complex insurance policies that may not deliver...
Read Full Story »
Tags: cyber security, data breach, data management
Posted in: Cyber Security, Solutions
June 2nd, 2025 by Roger Wentowski
The Rising Tide of Cyber Threats
From sophisticated ransomware attacks to subtle data breaches, the digital realm has become a battlefield where the stakes are higher than ever. As we navigate this complex terrain, one thing becomes crystal clear: robust...
Read Full Story »
Tags: business, cyber security, solutions, support
Posted in: Cyber Security, Solutions
May 3rd, 2025 by William Wentowski
The Ever-Evolving Threat Landscape
From sophisticated ransomware attacks to stealthy data breaches, the digital landscape is fraught with peril. As technology advances, so do the tactics of cybercriminals, leaving many organizations vulnerable and...
Read Full Story »
Tags: business, managed solutions, solutions
Posted in: Cyber Security, Managed IT
March 20th, 2025 by Roger Wentowski
The Ever-Evolving Threat Landscape
In today's digital age, cybersecurity threats are becoming increasingly sophisticated and persistent. Businesses of all sizes face a constant barrage of attacks from cybercriminals seeking to exploit...
Read Full Story »
Tags: business, cyber security, managed solutions
Posted in: Cyber Security
March 6th, 2025 by Roger Wentowski
The Digital Battlefield
In an era where digital transformation is no longer optional but essential, businesses face an ever-evolving landscape of cyber threats. From sophisticated ransomware attacks to subtle data breaches, the digital realm has...
Read Full Story »
Tags: antivirus, cyber security, solutions
Posted in: Cyber Security
February 23rd, 2025 by William Wentowski
You invested in the latest security software and even hired a great IT team. However, one misstep by an unsuspecting employee and a wrong click on a malicious link later, you are staring at a costly breach that threatens to jeopardize the future of...
Read Full Story »
Tags: assessment, business, cyber security
Posted in: Cyber Security
February 9th, 2025 by Roger Wentowski
When you think about cybersecurity, your mind might jump to firewalls, antivirus software or the latest security tools. But let’s take a step back—what about your team? The reality is that even with the best technology, your business is only as secure...
Read Full Story »
Tags: business, cyber security, solutions
Posted in: Cyber Security
February 3rd, 2025 by Roger Wentowski
The importance of robust cybersecurity cannot be overstated. As cyber threats evolve and multiply, businesses of all sizes find themselves in the crosshairs of malicious actors. This is where Managed Security Services (MSS) come into play, offering...
Read Full Story »
Tags: connectivity, cyber security, managed solutions
Posted in: Cyber Security
January 26th, 2025 by William Wentowski
Running a business is like being in the driver’s seat of a high-performance car. It’s fast-paced, competitive and full of passion. But even the best racecars can’t go far without regular pitstops.
Skipping those important checks is like failing to...
Read Full Story »
Tags: assessment, business, cyber security
Posted in: Cyber Security
January 15th, 2025 by William Wentowski
Despite believing they were immune, a small law firm in Maryland fell victim to a ransomware attack. Similarly, an accounting firm in the Midwest lost all access to its client information, financial records and tax files. They assumed that antivirus...
Read Full Story »
Tags: assessment, business, cyber security
Posted in: Cyber Security
January 6th, 2025 by William Wentowski
The Critical Need for Robust Cybersecurity
The importance of cybersecurity cannot be overstated. As businesses increasingly rely on technology to drive operations and store sensitive data, the threat of cyberattacks looms larger than ever. From data...
Read Full Story »
Tags: cyber security, data breach, data management
Posted in: Cyber Security
December 5th, 2024 by Roger Wentowski
In today's digital age, the threat of cyber attacks is more real and dangerous than ever before. From large corporations to small businesses, no one is immune to the risk of data breaches, malware infections, and other malicious cyber activities. The...
Read Full Story »
Tags: cyber security, dark web, data breach
Posted in: Cyber Security
November 20th, 2024 by Brian Wakefield
In today's digital age, cyber threats are an ever-present reality for businesses of all sizes. From data breaches and malware attacks to phishing scams and ransomware incidents, the risks posed by cybercriminals are constantly evolving. At BTS Technologies,...
Read Full Story »
Tags: communication, cyber security, data management
Posted in: Cyber Security
November 17th, 2024 by Roger Wentowski
As a business owner or manager, you lie awake at night worrying about protecting your critical data and keeping your operations running in the face of a potential disaster. Data loss can ruin a company - in fact, a staggering 80% of businesses that...
Read Full Story »
Tags: communication, cyber security, SleepEZ
Posted in: Cyber Security
October 23rd, 2024 by William Wentowski
Cyber insurance is an invaluable tool in your risk management arsenal. Think of it as one of the many weapons you have against cyberthreats. However, there's a widespread misconception that having cyber insurance is enough. The truth is—without a comprehensive...
Read Full Story »
Tags: business, cyber security, data management
Posted in: Cyber Security
October 16th, 2024 by Brian Wakefield
Imagine starting your day with a cup of coffee, ready to tackle your to-do list, when an email that appears to be from a trusted partner lands in your inbox. It looks legitimate, but hidden within is a phishing trap set by cybercriminals.
This...
Read Full Story »
Tags: communication, firewall, phishing
Posted in: Cyber Security
October 10th, 2024 by Jason Thompson
You might be thinking that you’ve done everything to protect your business from cyberthreats. You have the most advanced security solutions to defend against external threats, but are you equally protected against internal threats?
Knowingly or...
Read Full Story »
Tags: communication, data breach, firewall
Posted in: Cyber Security
September 2nd, 2024 by William Wentowski
In the ever-evolving digital landscape, cyber threats lurk around every corner, posing imminent risks to businesses of all sizes. From data breaches that can compromise sensitive information to ransomware attacks that can cripple operations, the consequences...
Read Full Story »
Tags: business, cyber security, data breach
Posted in: Cyber Security
June 3rd, 2024 by William Wentowski
The healthcare industry relies heavily on data and interconnected systems to deliver critical services and save lives. However, the sensitive nature of this information and the increasing sophistication of cyber threats make healthcare organizations...
Read Full Story »
Tags: cyber security, managed solutions, ransomware
Posted in: Cyber Security
May 28th, 2024 by William Wentowski
As a Client Chief Information Officer (CIO) at BTS Technologies, I have a front-row seat to the rapidly changing world of cybersecurity. The landscape is evolving at an unprecedented pace, and staying ahead of the curve is not just a necessity—it’s a...
Read Full Story »
Tags: communication, cyber security, data breach
Posted in: Cyber Security
May 7th, 2024 by William Wentowski
In today's rapidly evolving digital landscape, security has become a paramount concern for businesses of all sizes. With the increasing frequency and sophistication of cyber threats, protecting sensitive data, systems, and networks has become a daunting...
Read Full Story »
Tags: cost efficiencies, cyber security, data breach, infrastructure, scalability
Posted in: Cyber Security
May 3rd, 2024 by William Wentowski
In today's interconnected world, where digital technology permeates every aspect of our lives, the importance of cyber security cannot be overstated. A single data breach or cyber attack can have far-reaching consequences, compromising sensitive...
Read Full Story »
Tags: communication, cyber security, data breach
Posted in: Cyber Security
April 17th, 2024 by William Wentowski
In the digital age, ensuring the safety and integrity of data has become paramount for individuals and businesses alike. Cloud security emerges as a key player in this arena, offering robust solutions that strengthen our defense against cyber threats....
Read Full Story »
Tags: cloud, communication, data breach
Posted in: Cyber Security
April 1st, 2024 by William Wentowski
Picture this: Your computer suddenly locks you out, and a sinister message pops up demanding a hefty ransom for the return of your precious data. Sounds like a plot twist in a tech thriller, right? Well, welcome to the wild world of ransomware...
Read Full Story »
Tags: cyber security, email, ransomware
Posted in: Cyber Security
March 21st, 2024 by William Wentowski
In today's digital age, where data is a foundational asset for businesses and individuals alike, protecting this data becomes paramount. This is where data backup and disaster recovery come into play.
Understanding these terms and their significance...
Read Full Story »
Tags: backup and disaster recovery, cyber security, passwords
Posted in: Cyber Security
February 1st, 2024 by William Wentowski
In the ever-evolving landscape of cybersecurity threats, one malicious tactic stands out as a constant menace: phishing attacks. These deceptive maneuvers have become increasingly sophisticated, targeting individuals and organizations alike.
...
Read Full Story »
Tags: dark web, data breach, phishing
Posted in: Cyber Security
December 4th, 2023 by William Wentowski
The digital revolution is taking the world by storm. Everyone depends on computerized systems for managing daily activities, from small to large organizations, corporations, and governments. This makes cybersecurity a much-needed safeguard option...
Read Full Story »
Tags: cloud, cyber security, phishing, ransomware
Posted in: Cyber Security, Managed IT, Solutions
November 1st, 2023 by William Wentowski
In an age where nearly every aspect of business is conducted online, cybersecurity has become an essential component of any company's operations, regardless of size.
While larger enterprises typically have entire teams assigned to cybersecurity...
Read Full Story »
Tags: cost efficiencies, cyber security, productivity
Posted in: Cyber Security
October 3rd, 2023 by William Wentowski
The need for strong cyber security measures cannot be emphasized in today's linked digital environment. With the increased frequency and advancement of cyber-attacks, businesses must proactively protect their digital assets and sensitive data. A...
Read Full Story »
Tags: cost efficiencies, cyber security, productivity
Posted in: Cyber Security
September 1st, 2023 by William Wentowski
In an era where data breaches and cyber threats loom large, businesses are constantly seeking robust and reliable solutions to fortify their digital assets.
Microsoft Azure, a cloud computing platform by tech giant Microsoft, stands out for...
Read Full Story »
Tags: Azure, cyber security, managed solutions
Posted in: Cyber Security
August 21st, 2023 by William Wentowski
Cyber security dangers are a serious concern in today's quickly changing digital environment. Ransomware attacks and data breaches are two of the most frequent and harmful dangers businesses encounter. While both can have negative effects, their...
Read Full Story »
Tags: cyber security, data breach, ransomware
Posted in: Cyber Security
July 25th, 2023 by William Wentowski
In today's digital age, the healthcare industry has witnessed a remarkable transformation, with technological advancements revolutionizing patient care and administrative processes. Electronic health records, interconnected medical devices, and telemedicine...
Read Full Story »
Tags: backup and disaster recovery, cyber security, healthcare
Posted in: Cyber Security
June 16th, 2023 by William Wentowski
Cybersecurity is an integral part of running any business, regardless of its size. As technology advances and becomes more accessible, small businesses are becoming increasingly vulnerable to cyber-attacks. Cybercriminals target...
Read Full Story »
Tags: backup and disaster recovery, customer service, cyber security
Posted in: Cyber Security
June 1st, 2023 by William Wentowski
Backup and disaster recovery (BDR) is critical to any business's IT infrastructure. It helps protect against data loss and other disasters that could potentially cripple an organization. BDR solutions involve:
Backing up data regularly.
Storing...
Read Full Story »
Tags: backup and disaster recovery, cyber security, help desk
Posted in: Cyber Security
June 1st, 2023 by William Wentowski
Network monitoring is the process of tracking and managing all of the activities associated with a computer network, including data flows, performance levels, user access, and more. It involves gathering information from a variety...
Read Full Story »
Tags: cyber security, monitoring, network infrastructure
Posted in: Cyber Security
May 10th, 2023 by Roger Wentowski
Phishing scams are one of the most common forms of cybercrime today and can be incredibly damaging. The internet has opened up a whole new world for scammers to exploit unsuspecting victims by sending out fraudulent emails, texts, and other messages...
Read Full Story »
Tags: cyber security, Managed IT, phishing
Posted in: Cyber Security
April 24th, 2023 by Brian Wakefield
Cyber-attacks are becoming increasingly common as technology advances and more people are connected to the internet. Cyber-attackers can access personal data, exploit system vulnerabilities, and infect systems with malicious software that can cause...
Read Full Story »
Tags: cyber security, malware, phishing, ransomware
Posted in: Cyber Security
March 17th, 2023 by William Wentowski
As technology continues to develop, so does the potential for cyber security threats. With each new technological advancement comes a new wave of cyber security trends and strategies that must be addressed in order to keep data safe. In 2023, we can...
Read Full Story »
Tags: artificial intelligence (AI), cloud, cyber security, dark web, mobile device security, monitoring
Posted in: Cyber Security
February 17th, 2023 by Roger Wentowski
Healthcare organizations need cybersecurity. The healthcare industry is becoming more digital and, thus, a larger target for cyber-attacks. These attacks can have any including ransomware, phishing scams, malware, and other malicious activities that...
Read Full Story »
Tags: antivirus, cyber security, healthcare, malware, Managed IT, passwords, phishing, ransomware
Posted in: Cyber Security
November 29th, 2022 by Brian Wakefield
There are several reasons why businesses should take cyber security seriously, and some of the many benefits they can gain include the following:
Protects your online information: By having cyber security in place, you can help protect your important...
Read Full Story »
Tags: cyber security, dark web, data breach, malware, Managed IT, phishing, ransomware
Posted in: Cyber Security
October 11th, 2022 by Roger Wentowski
Undoubtedly, technological advancements have made work and everyday life so much easier. However, with increasing technology, the threat to the security of those who use such technologies remains.
BTS understands that a company's data security is of...
Read Full Story »
Tags: cyber security, data breach, malware, phishing, productivity, ransomware
Posted in: Cyber Security
August 12th, 2022 by Roger Wentowski
While you might have taken the strongest measures to ensure that your house remains safe and no burglar enters it, have you done the same for your business?
The risk of a cyber security threat is something that we cannot deny. Over the years, with...
Read Full Story »
Tags: antivirus, cyber security, data breach, malware, phishing, ransomware
Posted in: Cyber Security
July 17th, 2022 by Brian Wakefield
The world of technology has evolved majorly over the years. However, while technology has advanced, the risk of cyber-attacks has increased too. Businesses these days function fully on computers. While protective strategies like firewall and cloud services...
Read Full Story »
Tags: cyber security
Posted in: Cyber Security
June 17th, 2022 by William Wentowski
Cyber security helps safeguard your business against any potential attacks, malicious spyware, and data losses. With the continuous evolution of technology, more businesses are shifting toward digital platforms. While this has expanded the...
Read Full Story »
Tags: backup and disaster recovery, cloud, customer service, data breach, productivity
Posted in: Cyber Security
April 25th, 2022 by William Wentowski
Cyber security solutions are critical for all organizations, especially when you consider how critical digital and online technologies are to your day-to-day operations. Cybercrime is increasing daily, and several small companies are particularly susceptible...
Read Full Story »
Tags: backup and disaster recovery, cost efficiencies, regulation, Software-as-a-Service (SaaS)
Posted in: Cyber Security
April 4th, 2022 by William Wentowski
When turmoil and political upheaval wreak havoc half a world away, it is easy to think that your business is safe and sound here in America. Unfortunately, that is never the case, and is when you should be revamping your cyber security and examining...
Read Full Story »
Tags: data breach, multi-factor authentication (MFA), ransomware
Posted in: Cyber Security
March 15th, 2022 by Brian Wakefield
Small and medium-sized business owners often choose to outsource their IT services for all the right reasons. Not only does it help them get instant access to the best technologies and a qualified team of IT experts that supervise their...
Read Full Story »
Tags: cost efficiencies, Managed Service Provider (MSP), network infrastructure, SMBs, tips and tricks
Posted in: Cyber Security, Managed IT
February 22nd, 2022 by William Wentowski
Cyber security helps safeguard your business against potential attacks, malicious spyware, and data losses. With the continuous evolution of technology, more businesses are shifting toward digital platforms. While this has expanded the target audience,...
Read Full Story »
Tags: antivirus, cloud, data breach
Posted in: Cyber Security
February 7th, 2022 by William Wentowski
Everything humans do now is recorded in digital form, and this data may either be beneficial or harmful depending on how it is used. When it comes to the digital trace, there's a lot of common ground to draw on.
This article will help you understand...
Read Full Story »
Tags: data breach, firewall, network infrastructure
Posted in: Cyber Security
January 31st, 2022 by Brian Wakefield
Cyber security solutions are essential for businesses, especially given the importance of digital and internet technology in day-to-day functioning. Cybercrime is on the rise, and numerous small businesses are particularly vulnerable owing to a lack...
Read Full Story »
Tags: antivirus, firewall, productivity, ransomware, WiFi
Posted in: Cyber Security
January 27th, 2022 by Technology Assurance Group
Leading Managed Technology Services
Provider Shares Significant Findings
About IT Growth
BIRMINGHAM, AL – BTS, a leading managed
technology services provider
(MTSP), recently shared that IT
research and consulting...
Read Full Story »
Tags: cloud, Managed Service Provider (MSP), ransomware, SMBs, Technology Assurance Group (TAG)
Posted in: Cyber Security, Managed IT, Press Releases
January 23rd, 2022 by William Wentowski
Healthcare companies continuously face cyber threats that increases the safety risk of their patient information. Unfortunately, many healthcare leaders view cyber security as a technical issues that must be dealt with by the IT department.
The importance...
Read Full Story »
Tags: healthcare, HIPAA, multi-factor authentication (MFA), NIST, regulation
Posted in: Cyber Security
January 13th, 2022 by Technology Assurance Group
Leading MTSP Increases Their Customers’ Productivity with New Microsoft Applications
BIRMINGHAM, AL – BTS a leading managed technology services provider (MTSP), is preparing small to mid-sized businesses (SMBs) to upgrade their operating...
Read Full Story »
Tags: collaboration tools, Microsoft, SMBs, Technology Assurance Group (TAG), updates & upgrades, Windows
Posted in: Cyber Security, Press Releases
January 6th, 2022 by William Wentowski
Did you know that 96 percent of phishing attacks are carried via email? The other three percent are carried through phone or malicious websites. According to a research study, one in every 4,200 emails is phishing emails.
Moreover, a report by iC3 shows...
Read Full Story »
Tags: educational, email, phishing
Posted in: Cyber Security
December 10th, 2021 by William Wentowski
Cyber security is certainly a cause of stress for many business owners but it can protect them from data breaches that can otherwise cost them millions. In today's digital age, when cyberattacks are on the rise, businesses can’t afford to neglect...
Read Full Story »
Tags: educational, malware, phishing, support
Posted in: Cyber Security
November 30th, 2021 by Roger Wentowski
With the ransomware epidemic still in full swing, and with no clear end in sight, many CEOs are still scratching their heads with decisions on how to secure their network. They pivot from strategy to strategy, try to take on the burden solely in...
Read Full Story »
Tags: backup and disaster recovery, multi-factor authentication (MFA), ransomware, training, updates & upgrades
Posted in: Cyber Security
November 23rd, 2021 by Roger Wentowski
No matter your business scope, size, or industry, invest in cyber security audits routinely if you want to improve your company's security. Cyber security audits are more crucial than ever. A cyber security audit is primarily an independent...
Read Full Story »
Tags: audits, data breach, HIPAA
Posted in: Cyber Security
November 9th, 2021 by Brian Wakefield
Are you a small or medium-sized business owner looking for breakthrough growth and a boost to business performance? Consider partnering with a managed IT services provider. Post-COVID 19, small and medium-sized businesses have been in a...
Read Full Story »
Tags: backup and disaster recovery, cost efficiencies, email, network infrastructure, phishing, SMBs, updates & upgrades
Posted in: Cyber Security, Managed IT
November 1st, 2021 by William Wentowski
In the wake of the pandemic, employers across industries have given their employees the flexibility to work remotely. However, with the arrival of the COVID-19 vaccine, it is believed that many employees will either choose to work remotely or opt...
Read Full Story »
Tags: multi-factor authentication (MFA), tips and tricks, training, virtual private network (VPN)
Posted in: Cyber Security, Hybrid / Remote Workforce
October 20th, 2021 by Technology Assurance Group
Leading Managed Technology Services
Provider Invests in Advanced
Cybersecurity Tools
BIRMINGHAM, AL – BTS, a leading managed
technology services provider (MTSP),
has increased their investments in an
advanced cybersecurity...
Read Full Story »
Tags: collaboration tools, data breach, ransomware, Software-as-a-Service (SaaS)
Posted in: Cyber Security, Press Releases
October 4th, 2021 by William Wentowski
Cybercrime is growing faster than you think. Did you know that there is a hacker attack every 39 seconds affecting one in three Americans annually? Also, 64 percent of the companies in the US have experienced web-based cyber-attacks, including...
Read Full Story »
Tags: data breach, email, malware, network infrastructure, phishing, ransomware
Posted in: Cyber Security
September 23rd, 2021 by Brian Wakefield
Due to ongoing technological advancements and new business challenges cropping up now and then, business owners need to ensure that they have the best technologies in place. This is why it is essential to find a reliable and seasoned MSP (Managed Service...
Read Full Story »
Tags: backup and disaster recovery, cloud, IT consulting, Managed Service Provider (MSP)
Posted in: VoIP, Cyber Security, Managed IT
September 15th, 2021 by Technology Assurance Group
Leading Managed Technology Services
Provider Keeps SMBs Safe, Once
Again
BIRMINGHAM, AL – BTS, a leading managed
technology services provider
(MTSP), recently shared that their
robust cybersecurity solutions have...
Read Full Story »
Tags: cost efficiencies, data breach, ransomware, SMBs
Posted in: Cyber Security, Press Releases
September 7th, 2021 by William Wentowski
Cybercrime is growing faster than you might think. The internet has become a space that is continuously being attacked by malicious links, viruses, and Trojans. Whether you are self-employed, run a small business, or a large organization, you...
Read Full Story »
Tags: antivirus, email, Microsoft, passwords, phishing, updates & upgrades, Windows
Posted in: Cyber Security
August 11th, 2021 by William Wentowski
It's a Friday afternoon and you receive an email asking you to participate in a bid with a link to the bid documents. Maybe you will look at it before the weekend and mull over if you want to respond to it. Upon clicking the link,...
Read Full Story »
Tags: email, phishing, tips and tricks, training
Posted in: Cyber Security
August 9th, 2021 by William Wentowski
Regardless of the size, scope, or industry, every business is at the risk of cyber attacks. Corporations across industries are vulnerable because a majority of their data is stored online. From data breaches to infiltration on infrastructure and...
Read Full Story »
Tags: data breach, malware, NIST, phishing
Posted in: Cyber Security
August 4th, 2021 by Technology Assurance Group
Leading Managed Technology Services Provider Shares How SMBs Can Protect Themselves from Cyberattacks and Ransomware Threats
BIRMINGHAM, AL -BTS Technologies, Inc., a leading managed technology services provider (MTSP), recently shared that some...
Read Full Story »
Tags: antivirus, backup and disaster recovery, multi-factor authentication (MFA), SMBs, training
Posted in: Cyber Security, Press Releases
June 29th, 2021 by Technology Assurance Group
Leading Managed Technology Services Provider Shares How AI is
Evolving SMB Defenses
BIRMINGHAM, AL - BTS a leading managed technology
services provider (MTSP), announced today that AI (artificial intelligence) is starting to play a key role in cybersecurity...
Read Full Story »
Tags: artificial intelligence (AI), network infrastructure, SMBs, Software-as-a-Service (SaaS), Technology Assurance Group (TAG)
Posted in: Cyber Security, Press Releases
June 2nd, 2021 by William Wentowski
For the past several years, BTS has advocated the importance of cyber security. We've done our best to let businesses know that cyber security is something that can't be ignored or underbudgeted. However, more and more businesses fall victim to...
Read Full Story »
Tags: backup and disaster recovery, data breach, ransomware
Posted in: Cyber Security
May 25th, 2021 by William Wentowski
The events happening with Colonial Pipeline are nothing new. Businesses are hacked every day, however, few have as much impact on the individual citizen as an attack on vital infrastructure. Over the past year, ransomware attacks have increased 300%....
Read Full Story »
Tags: backup and disaster recovery, data breach, monitoring, ransomware
Posted in: Cyber Security
May 7th, 2021 by Matt Dean
Many organizations have heard of the cloud; the mythical technology that few grasp, but know it’s where their business needs to move. Like any buzzword or acronym, it is meant to excite and ensure it’s on the tip of everyone’s tongue. But many organizations...
Read Full Story »
Tags: cloud, training, updates & upgrades, virtual private network (VPN)
Posted in: Cyber Security, Managed IT, Hybrid / Remote Workforce
May 4th, 2021 by Technology Assurance Group
Startling Statistics Reveal Challenges of Healthcare Industry's Ability to Safeguard Patient Records
BIRMINGHAM, AL - BTS Technologies, Inc., a leading managed technology services provider, announced that the company is helping healthcare...
Read Full Story »
Tags: data breach, healthcare, HIPAA
Posted in: Cyber Security, Press Releases
April 30th, 2021 by Roger Wentowski
Are you prepared for the unthinkable? As Accounting and Financial professionals, we are accountable for some of the most important information our companies have. Are you prepared? Do you have the best controls in place to help prevent a hacker from...
Read Full Story »
Tags: backup and disaster recovery, data breach
Posted in: Cyber Security
April 22nd, 2021 by Roger Wentowski
When it comes to business technology and services, there is one undeniable truth. You get what you pay for. If you find a cheaper service somewhere else, there's probably a reason why it costs less. Let's take cyber security, a costly (but necessary)...
Read Full Story »
Tags: cost efficiencies
Posted in: Cyber Security
April 14th, 2021 by Brian Wakefield
This January, the HIPAA Safe Harbor Bill became law, and it's changing how all medical practices and healthcare organizations need to approach their cyber security. Here's what the law does and how it can affect your business:
HIPAA Safe Harbor Law...
Read Full Story »
Tags: healthcare, HIPAA, NIST, regulation
Posted in: Cyber Security, News
April 13th, 2021 by Technology Assurance Group
BTS Helps Customers Protect Their Precious Networks
BIRMINGHAM, AL – BTS a leading managed
technology services provider
(MTSP), proactively helps
...
Read Full Story »
Tags: malware, multi-factor authentication (MFA), phishing, SMBs
Posted in: Cyber Security, Press Releases
March 24th, 2021 by William Wentowski
Cyber crime continues to increase in frequency and has become a growing concern for businesses everywhere. While this has lead to increased adoption of cyber security solutions, the rate of cyber crime has not slowed down. Why do businesses keep...
Read Full Story »
Tags: cost efficiencies, data breach, malware, passwords, phishing, ransomware
Posted in: Cyber Security
February 3rd, 2021 by William Wentowski
It is no secret that new dangers plague every industry when regarding cyber security. Everyday there is a new ransomware or crypto virus will grind day to day activities to a halt. Even with the great strides in security the past few years, many companies...
Read Full Story »
Tags: dark web, email, phishing, ransomware, training
Posted in: Cyber Security
January 11th, 2021 by Technology Assurance Group
BIRMINGHAM, AL – BTS Technologies, Inc., a
leading managed technology services
provider (MTSP), announced today
that it is educating companies on the
dramatic spike in cybercrime
targeted towards small to mid-sized
(SMB) businesses. Cybersecurity...
Read Full Story »
Tags: data breach, ransomware, SMBs, Technology Assurance Group (TAG)
Posted in: Cyber Security, Press Releases
October 29th, 2020 by William Wentowski
The Cybersecurity & Infrastructure Security Agency (CISA) has issued an alert for increased Ransomware activity targeting Healthcare and the Public Sector. During COVID-19, we have seen increased attempts to utilize ransomware on healthcare providers....
Read Full Story »
Tags: data breach, email, healthcare, ransomware
Posted in: Cyber Security
September 18th, 2020 by Technology Assurance Group
BTS, a leading managed
technology services provider
(MTSP) announced today that the
company is preparing small to midsized business (SMB) owners on
what to expect in the workplace,
after the pandemic. With people
working from home in droves,
there is...
Read Full Story »
Tags: pandemic, partnership, SMBs, Technology Assurance Group (TAG)
Posted in: Cyber Security, Hybrid / Remote Workforce, Press Releases
June 8th, 2020 by Roger Wentowski
Now that businesses are working remotely, they need a way to ensure their network is protected and that their employees are able to efficiently complete work-related tasks. While some companies may be using a VPN to accomplish this, problems arise...
Read Full Story »
Tags: backup and disaster recovery, cloud, cost efficiencies, virtual private network (VPN)
Posted in: Cyber Security, Hybrid / Remote Workforce
June 3rd, 2020 by Technology Assurance Group
BIRMINGHAM, AL - BTS, a leading managed technology services provider (MTSP), announced today that the company is providing home office cybersecurity for remote workers to support them through the current pandemic and beyond. According to a BitSight...
Read Full Story »
Tags: pandemic, SMBs
Posted in: Cyber Security, Hybrid / Remote Workforce, Press Releases
April 16th, 2020 by William Wentowski
Cybercrime is spiking dramatically alongside the COVID-19 pandemic. As they are leveraging not only the confusion it's causing but the fact that many IT and security providers are currently overwhelmed to their advantage. This has become especially...
Read Full Story »
Tags: malware, pandemic, phishing, training
Posted in: Cyber Security
February 5th, 2020 by Brian Wakefield
Anyone who runs a business can tell you the importance of keeping up to date with today's technology through IT. They can also tell you just how much an in house IT team will cost your business. The cost of hiring staff, research, development, and implementation...
Read Full Story »
Tags: cost efficiencies, help desk, monitoring
Posted in: Cyber Security, Managed IT
January 4th, 2020 by Technology Assurance Group
BIRMINGHAM, AL – BTS leverages sophisticated Dark Web intelligence technology to identify, analyze, and check for compromised customer and employee data. Cybercrime is rapidly on the rise in the United States and SMBs need to know if their information...
Read Full Story »
Tags: dark web, data breach, monitoring, passwords, Technology Assurance Group (TAG)
Posted in: Cyber Security, Press Releases
December 23rd, 2019 by William Wentowski
Cyberattacks are a common occurrence in today’s business world. Hopefully, your company has security measures and training in place to combat such attacks, but mistakes can be made. If your company is the victim of a cyberattack, do you know the...
Read Full Story »
Tags: data breach, multi-factor authentication (MFA), passwords, phishing, training
Posted in: Cyber Security
November 6th, 2019 by William Wentowski
Join BTS at the Hack & Attacks Cybersecurity Panel being hosted by the Birmingham Business Journal (BBJ) on Tuesday, November 12th, 2019 at the Birmingham Museum of Art.
(This event was rescheduled from it's original date on October 24th.)
The...
Read Full Story »
Tags: events
Posted in: Cyber Security
November 5th, 2019 by Technology Assurance Group
BIRMINGHAM, AL – BTS, a leading managed technology services provider (MTSP), announced today that the company has launched a Secure WiFi-as-a-Service program to protect its customers from cyber attacks through wireless access points. Over the...
Read Full Story »
Tags: SMBs, Technology Assurance Group (TAG), WiFi
Posted in: Cyber Security, Press Releases
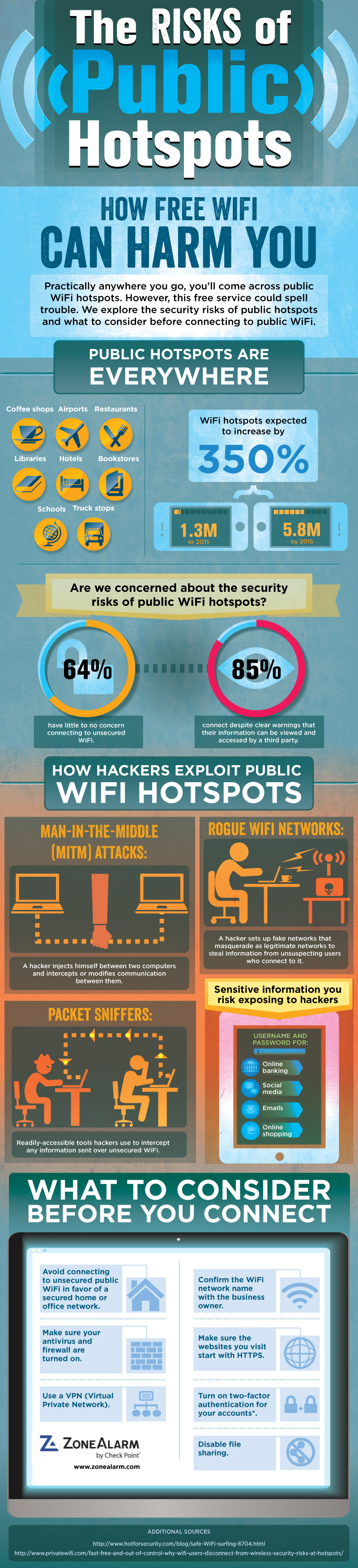
September 14th, 2019 by William Wentowski
Practically anywhere you go, you'll come across public WiFi hotspots. However, this free service could spell trouble. We explore the security risks of public hotspots and what to consider before connecting to public WiFi.
...
Read Full Story »
Tags: WiFi
Posted in: Cyber Security
June 19th, 2019 by William Wentowski
Artificial Intelligence (AI) is becoming one of the cutting-edge tools in the Cyber Security arms race. Criminals are using AI to accelerate the pace of attacks and provide ever more complex campaigns. This adoption of AI by the criminals is mirrored...
Read Full Story »
Tags: artificial intelligence (AI), malware, toolchains, WatchGuard
Posted in: Cyber Security
June 19th, 2019 by William Wentowski
Are you aware that BTS Technologies, Inc. has complete cybersecurity solutions to protect your organization from any threat or attack that could arise? Having poor security in your business can lead to not only vulnerability within your...
Read Full Story »
Tags: dark web, malware, monitoring, phishing, ransomware, SMBs
Posted in: Cyber Security
April 23rd, 2019 by William Wentowski
At BTS Technologies Inc. we work diligently to ensure that our customers are never hit with ransomware with our innovative firewall and preventative measures. But what should you do if you are hit with a ransom, and should you ever just pay the ransom?...
Read Full Story »
Tags: backup and disaster recovery, data breach, firewall, monitoring, ransomware
Posted in: Cyber Security
February 4th, 2019 by Technology Assurance Group
BIRMINGHAM, AL –
BTS a leading managed technology services provider (MTSP), is helping small to midsized businesses (SMBs) equip themselves with the necessary cybersecurity protections that every modern company needs to survive. Over the past,...
Read Full Story »
Tags: data breach, IT consulting, SMBs, Technology Assurance Group (TAG)
Posted in: Cyber Security, Press Releases
December 21st, 2018 by Technology Assurance Group
BIRMINGHAM, AL –
BTS a leading
managed technology services
provider (MTSP), is helping
small to mid-sized businesses
(SMBs) secure their
organizations from cyberattacks, by addressing the
Windows 7 “End of Life” policy
that will begin in January...
Read Full Story »
Tags: Managed Service Provider (MSP), Microsoft, SMBs, Technology Assurance Group (TAG), updates & upgrades, Windows
Posted in: Cyber Security, Managed IT, Press Releases
December 17th, 2018 by William Wentowski
Another day, another major data breach. These have become all too common, and every passing breach raises your risk of major theft and fraud. This time it is Marriott, a company that owns more than 1 in 15 of the hotel rooms worldwide (1.1 million rooms...
Read Full Story »
Tags: data breach, passwords, phishing
Posted in: Cyber Security
December 17th, 2018 by William Wentowski
This gigantic Marriott breach might not affect you directly—although there is small chance of that—but it highlights something very real and important for SMBs. The vector for this breach is rumored to be Marriott’s supply chain. Identifying the specific...
Read Full Story »
Tags: dark web, data breach, SMBs
Posted in: Cyber Security
December 17th, 2018 by William Wentowski
BTS is now offering Dark Web Scans to help round out our security offering. These scans can tell us when, where, and what information or credentials have been stolen so we can better protect your business and staff. If you are a Managed Service Partner,...
Read Full Story »
Tags: dark web, partnership
Posted in: Cyber Security
December 6th, 2018 by Roger Wentowski
Security should be a number one priority for any business. From cybersecurity to physical security, it can be a hassle having different providers managing your systems resulting in having various contracts and massive costs. But what if there was a...
Read Full Story »
Tags: SMBs
Posted in: Cyber Security, Surveillance
October 12th, 2018 by Technology Assurance Group
BIRMINGHAM, AL – BTS a leading managed
technology services provider
(MTSP), is helping small to midsized
businesses (SMBs) protect
themselves and their customers
from DNS (Domain Name Server)
attacks through innovative
technology solutions. As...
Read Full Story »
Tags: malware, Managed Service Provider (MSP), phishing, SMBs, Technology Assurance Group (TAG)
Posted in: Cyber Security, Press Releases
September 18th, 2018 by William Wentowski
Protecting Your Business from Phishing Attacks with WatchGuard Total Security Suite
Phishing attacks continue to be a top concern for small businesses and midsize enterprise organizations. In fact, 76% of businesses report being a victim of...
Read Full Story »
Tags: email, SMBs, training, WatchGuard
Posted in: Cyber Security
September 17th, 2018 by Technology Assurance Group
BIRMINGHAM, AL – BTS, a leading managed technology services provider (MTSP), is helping small to mid-sized businesses (SMBs) thwart cyberattacks and protect their organizations from unnecessary downtime by addressing the most common tactic that...
Read Full Story »
Tags: data breach, Managed Service Provider (MSP), passwords, phishing, SMBs, Technology Assurance Group (TAG)
Posted in: Cyber Security, Press Releases
August 6th, 2018 by Technology Assurance Group
BTS is helping small to mid-sized businesses (SMBs) navigate the recent changes in cybersecurity standards that are highly likely to affect American businesses. Many have heard about Facebook’s recent controversy around Cambridge Analytica and irresponsible...
Read Full Story »
Tags: data breach, email, regulation, Technology Assurance Group (TAG)
Posted in: Cyber Security, Press Releases
July 3rd, 2018 by Technology Assurance Group
BTS a leading managed technology services provider, is helping small to mid-sized businesses (SMBs) to prevent cryptojacking attacks from damaging their organizations. Cryptojacking attacks, are derived from the widely popular cryptocurrencies, such...
Read Full Story »
Tags: data breach, SMBs, Technology Assurance Group (TAG), virtual private network (VPN)
Posted in: Cyber Security
June 20th, 2018 by William Wentowski
Depending on your business, you’re likely creating much more data each day than you realize. That data can take on many different forms: bank transactions, budgets, personnel data, contracts, product designs, customer details, sales leads, progress...
Read Full Story »
Tags: backup and disaster recovery
Posted in: Cyber Security
March 29th, 2018 by Michael Gendreau
By Michael Gendreau
Being the newest member of the BTS family, I am constantly listening and observing the people and conversations around me. I came from the electrical contracting world and was like many CFOs in that the company’s Information Technology...
Read Full Story »
Tags: backup and disaster recovery, cost efficiencies, data breach, IT consulting, Managed Service Provider (MSP), SMBs
Posted in: Cyber Security, Managed IT
February 26th, 2018 by Technology Assurance Group
BTS a leader in managed technology services, announced today that the company has partnered with ID Agent, to enhance the security of SMBs (small to mid-sized businesses) across the nation. ID Agent and this partnership will enable business owners,...
Read Full Story »
Tags: dark web, partnership, SMBs, Technology Assurance Group (TAG)
Posted in: Cyber Security, Press Releases
January 31st, 2018 by William Wentowski
Security breaches can happen anytime to anyone. As a small to medium-sized business (SMB) you may assume that hackers will go after large corporations first where they will have access to the maximum amount of information possible, however,...
Read Full Story »
Tags: email, malware, phishing, SMBs
Posted in: Cyber Security
December 18th, 2017 by William Wentowski
WPA2 is widely regarded as the industry's most secure wireless encryption protocol. However, on October 16, 2017, the US-CERT announced several vulnerabilities in the WPA2 encryption implementation in clients and AP. Collectively called KRACKs (Key...
Read Full Story »
Tags: updates & upgrades, WatchGuard, WiFi
Posted in: Cyber Security
September 30th, 2017 by William Wentowski
We could make this a spooky Halloween themed article. It would get a few laughs, have some cheesy puns, and would be a grave (ha!) disservice to our customers. Companies are not doing enough for their cyber security, and it's not a corny joke.
(sorry)...
Read Full Story »
Tags: audits, data breach, network infrastructure, passwords
Posted in: Cyber Security
September 22nd, 2017 by Technology Assurance Group
BTS a leading provider of unified communications has announced that the company is certified to provide cybersecurity solutions to SMBs (small to mid-sized businesses) to protect them from the barrage of cyber-attacks that occur every day. Cybercrimes...
Read Full Story »
Tags: backup and disaster recovery, malware, phishing, ransomware, SMBs, Technology Assurance Group (TAG)
Posted in: Cyber Security
July 26th, 2017 by William Wentowski
As part of our larger efforts to help customers combat cyber threats, we are sharing our e-book - "5 Common Disasters that Strike Small Businesses." It is a quick overview of the, you guessed it, most common ways business data is stolen, damaged...
Read Full Story »
Tags: backup and disaster recovery, data breach, IT consulting, ransomware
Posted in: Cyber Security
July 12th, 2017 by William Wentowski
You may have recently seen reports on the news discussing recent IT attacks and malware prevention measures. These specials aim to inform and help protect users from inadvertently spreading threats or falling into cyber traps. We've also been sharing...
Read Full Story »
Tags: data breach, malware, phishing, ransomware
Posted in: Cyber Security
September 9th, 2015 by William Wentowski
Microsoft will no longer offer customer support on issues related to Microsoft Windows Server 2003. This encompasses all issues of infrastructure performance, capability, and security, which are all of obvious concern to business owners. This is a reflection...
Read Full Story »
Tags: Microsoft, Technology Assurance Group (TAG), updates & upgrades, Windows
Posted in: Cyber Security